Cloud adoption has continued to grow as more organisations implement a cloud-first strategy in support of digital transformations, mobility and IT agility. Organisations are at very different stages in their adoption, with a small percentage of organisations having more than half of their workloads in the public cloud.
Despite the relatively low percentage of workloads in the cloud so far, an impressive 77 per cent of enterprises have at least one application, or a portion of their infrastructure, in the cloud (IDG Cloud Computing Study, 2018). This broad adoption of the cloud suggests that the proportion of overall workloads delivered this way will increase with time as workloads are re-architected to suit the public cloud.
This article will look at how organisations can prepare for a
transition to the cloud and re-architect their security stack to enable
the benefits of the cloud, rather than restricting them.
Public Cloud Adoption
Organisations are moving to the cloud due to the high cost, agility, mobility and flexibility benefits it offers. Despite these benefits, public cloud adoption has been held back in some organisations due to considerations around security. The advantage of increased agility and flexibility in DevOps can result in poorly secured environments if proper governance is not well implemented. We can see examples of this in some of the most significant data breaches of 2018, such as the ISP that left 73GB of sensitive data in a public Amazon S3 Bucket.
In many cases, those familiar with the cloud have acknowledged that security is no longer a concern of the public cloud. The leading cloud service providers’ (CSPs) security resources dwarf that of any FTSE 100 company. The focus is now on how the organisation can make a secure transition without disrupting their current security model. When a security architecture is designed and implemented correctly, it can support the organisation’s requirements for more flexibility, scalability and a lower total cost of ownership.
Impact on Cybersecurity
In this article, we will look at hybrid security architectures that serve both on-premise and the public cloud. When we refer to “traditional” security architecture, we are referring to the range of security software and services that reside at the edge of the corporate network. When using this architecture, all Internet bound traffic must be proxied via the Security Edge where traffic is inspected and logged. This architecture is effectively a single choke point for all traffic to traverse. This results in a tight perimeter, good visibility, but significantly increased latency for Remote Offices and Mobile Workers when visiting websites and applications out on the Internet.
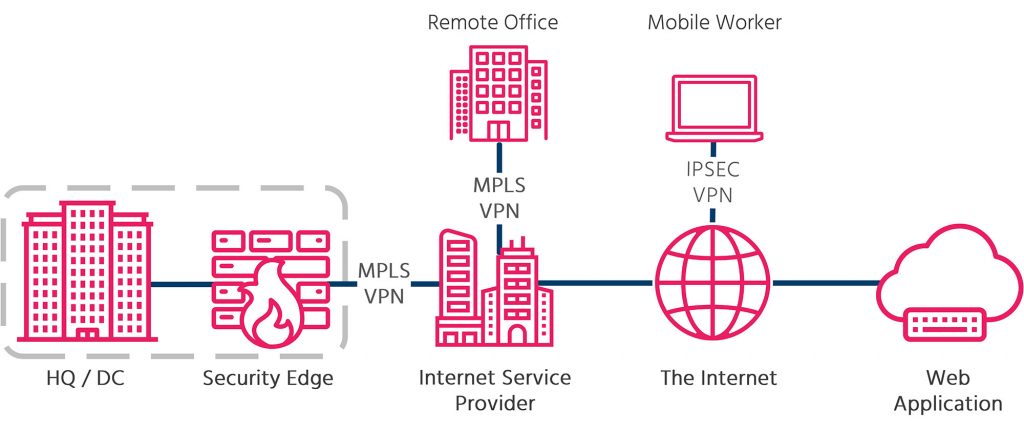
As most organisations are still in the process of migrating to the cloud, this model is still serving many enterprises well. However, as the ration of local to Internet traffic grows, the security edge will bottleneck Internet bound traffic and provide a poorer user experience for anyone not siting in the HQ / DC.
A common reason that organisations still use this architecture is a lack of understanding of the shared responsibility model for security in the public cloud. The responsibilities for On Premise, Infrastructure as a Service (IAAS), Platform as a Service (PAAS) and Software as a Service (SAAS) vary greatly as can be seen below.
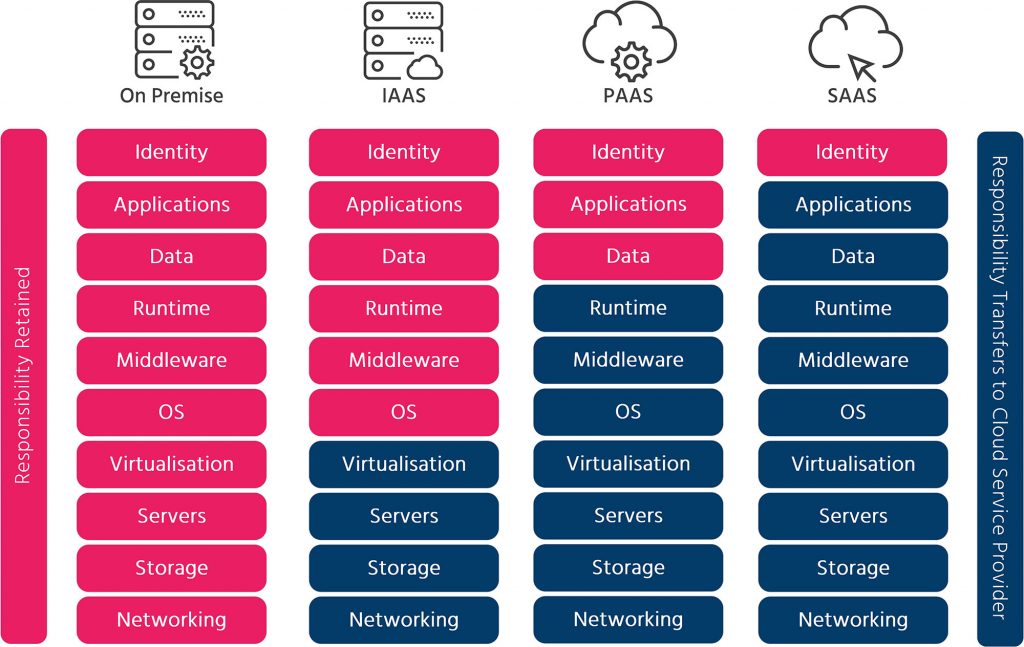
Responsibilities are further complicated as the number of parties involved grows to include not just CSP’s, but also managed security service providers (MSSPs) and vendors. Many organisations have taken what may seem like the default route, and started to extend their on-premise security technologies into the cloud. However, the traditional environment of an on-premise security stack cannot easily expand into the public cloud without losing some key benefits of cloud migration.
The result of expanding your traditional architecture into the public cloud is the loss of benefits such as cost and flexibility, key drivers for moving to the public cloud. Additionally, if the solution has not been designed to work optimally in the cloud, the integration may be poor and have a negative effect on visibility, having a compounding effect on all other controls.
Not only is the effectiveness of security compromised by this approach, but other benefits of adopting the public cloud are not realised. The total cost of ownership for the security function will increase significantly, and the scalability of the cloud function will be restricted by the capacity of the on-premise solutions. These effects are compounded when the adoption of multiple CSPs is considered.


Leave a Reply