On Monday, 13th July 2015 the Italian company ‘Hacking Team’, who design and develop surveillance software specifically to aid governments around the globe in hacking their own citizen’s devices, was itself the victim of a devastating hack.
The company has been shrouded in controversy since Paris-based Reporters Without Borders listed it as a ‘Corporate Enemy’ of the Internet in 2013. The list consisted of ‘Digital Mercenaries’ that have sold their surveillance software to authoritarian regimes. Hacking Team has repeatedly denied all allegations of selling their software to blacklisted countries; until now, no one could prove otherwise.
“On the issue of repressive regimes, Hacking Team goes to great lengths to assure that our software is not sold to governments that are blacklisted by the EU, the US, NATO, and similar international organizations or any “repressive” regime.”
Eric Rabe, Hacking Team Senior Counsel
400 gigabytes of the company’s emails, internal documents, financial data and the source code for their software, was leaked through their own Twitter account, which was also compromised by the hackers. “Since we have nothing to hide, we’re publishing all our emails, files and source code,” the tweet said. The post has since been removed and the Twitter account was suspended until control of the account was regained.
Among the massive amount of data leaked was a spreadsheet that lists the company’s active and in-active clients. The list includes several European intelligence agencies, police forces, and bureaus. However, the European Union (EU), United Nations (UN) and the North Atlantic Treaty Organisation (NATO) had blacklisted multiple countries on the list. Some clients even had the privilege of being listed as “Not officially supported”. Countries such as Libya, Egypt, Ethiopia, Morocco, Sudan and Syria had all done business with the Hacking Team.
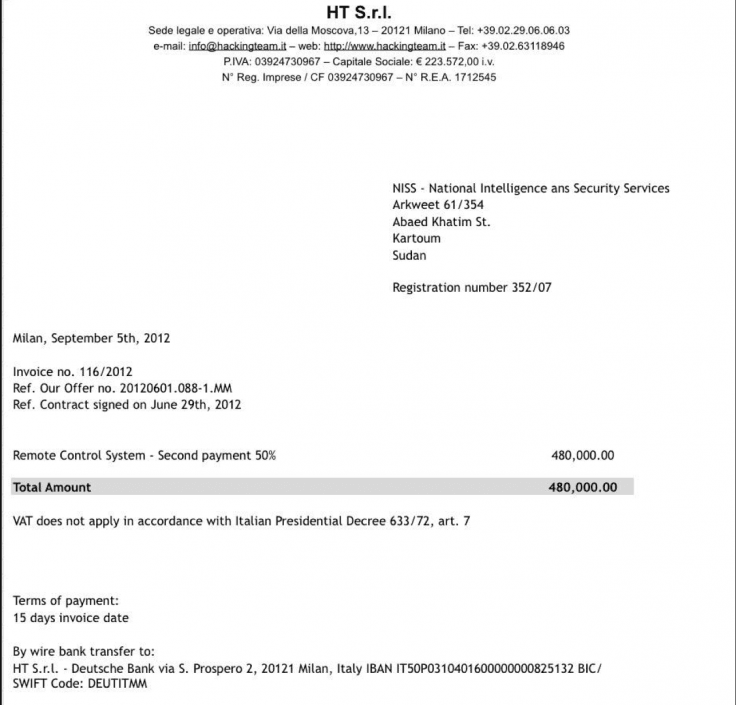
Selling Spyware to Sudan was perhaps one of the most controversial revelations of the hack. A report by Citizen Lab detailed that Hacking Team’s software was being used inside Sudan, which lead to a yearlong investigation by the UN; however, the spyware effectively stonewalled the investigation. Not only that, but an arms embargo enforced by the United Nations and the European Union prohibits selling “arms and related material” to Sudan. Hacking Team had previously denied these allegations and claims to have never done business with the country. However, the client list and recently uncovered invoice showing a payment from the Sudanese National Intelligence and Security Service for €480,00.00 would suggest otherwise.
It’s almost public knowledge that government agencies spy on citizens. Edward Snowden himself said spying is a necessity, as long as it’s justified, targeted and has a narrow scope. However, Hacking Teams Remote Control System (RCS) is clearly designed for mass surveillance.
“’Remote Control System’ can monitor from a few and up to hundreds of thousands of targets. The whole system can be managed by a single easy to use interface that simplifies day by day investigation activities”. Hacking Teams Remote Control System (RCS) Brochure
Sadly, in the hand of repressive regimes the main people targeted by this type of attack are Journalists, Political Activists, and Human Rights workers; who have learned that the Internet provides a platform for government regimes to spy on their every move.
Around the same time Hacking Team is reputed to have sold Spyware to Uzbekistan, Human Rights Watch reported that human rights activists, journalists and others imprisoned by the Uzbek Government were suffering torture and abysmal prison conditions. To further Uzbekistan’s abysmal human rights record, excessive force against protesters has also been reported on multiple occasions, with more than 170 people being killed in 2013.
David Vincenzetti, the CEO of Hacking Team, has recently spoken out in defense of the questionable decisions made by the company to sell to blacklisted countries, in what can only be described as a damage limitation exercise. Vincenzetti did admit a business relationship with Libya and Sudan but defended it stating “we did it when suddenly it seemed that the Libyans had become our best friends”. Vincenzetti added that the business with Sudan was carried out before the political arena and regulations changed.
“The geopolitical [landscape] changes rapidly, and sometimes situations evolve. But we do not trade in weapons, we do not sell guns that can be used for years. We’re the good guys.”
David Vincenzetti, Hacking Team CEO
A review of the company’s emails available on Wikileaks confirms that Vincenzetti has only added to the lies. The spoils of the Hacking Team leak have exposed the company’s dealings and shown the lengths to which their public relations campaign has gone to cover up the multitude of illegal dealings the company has been involved in. Do they really believe they are the good guys? Unsurprisingly, no.
“Imagine this: a leak on WikiLeaks showing YOU explaining the evilest technology on earth! You would be demonised by our dearest friends the activists, and normal people would point their fingers at you” –
David Vincenzetti, Hacking Team CEO in an internal email to Hacking Team staff on the 8th June, 2015
Take a look through the Hacking Team archives here


Leave a Reply